How doe’s Samsung remove FRP with internal tools.

I am asked almost every week this question. “How are remote unlocking services able to remove FRP from Samsung devices in a matter of seconds?” This question has taken me many hours of investigation to answer. The simple answer is that they are using Samsung’s official internal tools and server called GSPN. Samsung must have a method to deal with devices that are locked with FRP / Google account lock. Samsung is not going to lock themselves out a their own device. Below I am going to show the official method that Samsung uses. AT commands are the preferred means of communication with the device this is done over the device modem. All modems have a AT command interface and can communicate with this protocol. Phonlab has even developed a program we call Phonlab AT Command Injector which has a bunch of commands that we have discovered and is setup to talk with Samsung device. Samsung’s uses a cypher or encryption to accomplish this frp removal and for this reason the commands below only work on my device and only work on my device one time. But for educational reasons I think it will be helpful for many of you to see them and be able to investigate this a little yourself. Have fun. 🙂 I know I did. If you want to learn more about smartphones then check out our Phonlab smartphone tech course.
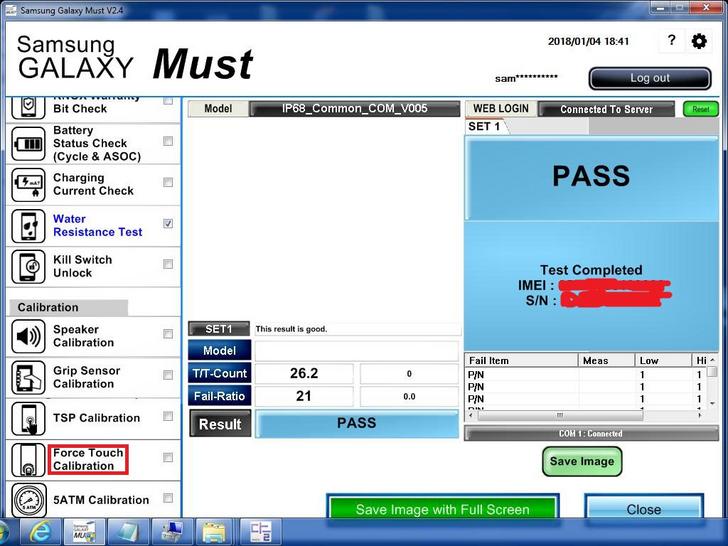
FRP removal is called KILL SWITCH UNLOCK by all OEM’s like you can see in the Picture above of Samsung Galaxy Must which is a internal tool that requires a login and password to use.
Commands are what is send from your PC to the device and Returns is what the device send back to the PC
Command AT
Return AT…OK..
Command AT+DEVCONINFO
Return AT+DEVCONINFO.+DEVCONINFO:
MN(SM-G955U);
BASE(SM-N900);
VER(G955USQU2CRB9/G955UOYN2CRB9/G955USQU2CRB9/G955USQU2CRB9);
HIDVER(G955USQU2CRB9/G955UOYN2CRB9/G955USQU2CRB9/G955USQU2CRB9);
MNC(260);
MCC(310);
PRD(TMB);;
OMCCODE();
SN(R2);
IMEI();
UN(9888D930);
PN();
CON(AT,MTP);
LOCK(NONE);
LIMIT(FALSE);
SDP(RUNTIME);
HVID(Data:196609,Cache:262145,System:327681);USER(GUEST)
..#OK#….OK
Command AT+REACTIVE=1,0,0
Return AT+REACTIVE=1,0,0..+REACTIVE:1,TRIGGERED….OK..
Command AT+REACTIVE=2,0,3AB235D2AA0B418AB65A8A02C9FA2E747A040508ED8ECA3D632F2695EA4F26C0
Return AT+REACTIVE=2,0,3AB235D2AA0B418AB65A8A02C9FA2E747A040508ED8ECA3D632F2695EA4F26C0..+REACTIVE:2,0000010000004603002079F84A1B0BE4D4E2F1F032FCFFE13AC583961C5094AD5B3A869E92EB8664FCCE0400205E82583881FD7422047C608EF204494D44926517E42AAB6A5CF458D6EF0974F6….OK..
Command AT+REACTIVE=2,0,53CDF83ACCD91D1D9BC809167892A861F006BFCB161285B5F7A958016B691B3C
Return AT+REACTIVE=2,0,53CDF83ACCD91D1D9BC809167892A861F006BFCB161285B5F7A958016B691B3C..+REACTIVE:2,000001000000460300204C8CF7B3F27CCA697DBF5D476A574E94B9EC591647486BB158B0D6D07CC244E00400205E82583881FD7422047C608EF204494D44926517E42AAB6A5CF458D6EF0974F6….OK..
Command AT+REACTIVE=2,1,010000012A0100011107002045F19E14B1831C160AB820FB2F2A1799253380D08BD3E6BA13E54D489A30920D06010019BF00B7CF80B9C25F0906E9225CAB84109F02E9C67CA6303B46E415CBC436B093409A79635F2D95B975E17A60E226AAA1E064DA72025C8FB3F0B254639496ECC663934CF3C001ED9E1816E0B1AFCA1C20FA72AF3A02208388766E4C6473E69BC529E6FC31BD258CC2F177E107FE28DB59E24E73E38A056959967DFB6717C2FB7114316DBE786F7B9FE15FDF667028F260ED78C2419F8BB68D1E495140D95D89B34492D55D3E0B132F7AF8E73B0294D759743EA256F759741B6A13CFF43319A19DCCB1A3DA60C09D23784D3E3A8874A814A2190156BF1E944B9B6F48F260BD6DE30FB2146ED03006324FC49D8E2EBD68243140DA703D28D38B18BB70C070AD5B
Return AT+REACTIVE=2,1,010000012A0100011107002045F19E14B1831C160AB820FB2F2A1799253380D08BD3E6BA13E54D48A30920D06010019BF00B7CF80B9C25F0906E9225CAB84109F02E9C67CA6303B46E415CBC436B09309A79635F2D95B975E17A60E226AAA1E064DA72025C8FB3F0B254639496ECC663934CF3C001ED9E1816E0B1AFCA1C20FA72AF3A02208388766E4C6473E69BC529E6FC31BD258CC2F177E107FE28DB59E24E73E38A056959967DFB6717C2FB7114316DBE786F7B9FE15FDF667028F260ED78C2419F8BB68D1E495140D95D89B34492D55D3E0B132F7AF8E73B0294D759743EA256F759741B6A13CFF43319A19DCCB1A3DA60C09D23784D3E3A8874A814A2190156BF1E944B9B6F48F260BD6DE30FB2146ED03006324FC49D8E2EBD68243140DA703D28D38B18BB70C070AD5B..+REACTIVE:2,OK….OK..
RootJunky out.


5 Responses
Learning about AT commands has been a real adventure. 🙂
HOW did you or Where did you get the hashcodes You Inserted into your Reactivate commands?
great question. you need to enroll in our phonlab smartphone Tech course to learn more about that.
Hello RJ & Team,
So, i recently stumbled upon this gem you offer, and I have just a couple questions:
1. I seen you’re from/based in Indiana, do you offer in-person classes? or is it online only?
2. Will the FRP class teach me to remove the FRP lock, like premium tools/boxes/servers are able to( ex: Ma**aTool, S**Hub Tool, ChimeraTool) ? Or does it only teach basics, like how the process is done, but not how to solve the questions, or how to calculate and return the correct response for removal?
I hope I made sense, and the questions is understandable. I am not a dev, but have used several boxes/dongle/server tool. And finding understandable, let alone, if any at all, guides or anything to learn this is near impossible or is all classes im the middle-east.
I know for me, if there was a dev/box team from the US, i wouldnt mind as much in supporting and paying for the tools. But with these unknown dev teams from over-seas, ive faced issue and problem, one after another, from no support, to servers going down, lost credits etc. and would love to learn how its done, to do it myself.
Also, if offer in person classes, what city/area are you located in Indiana (if IN is even the correct state)?
Extremely excited to hear from you, and maybe even enroll soon!
thanks
UKG
Dear RootJunky. Thanks for excellent article about Samsung Galaxy Must. Following your comments, I have tested with Galaxy Note 9 (SM-N960N). Realterm is used for “send”ing modem AT commands to android phone.
For ATD010376135xx\r\n(attention dialing phone number with return), proper dialing with return OK without screen lock, and no response in case of screen lock. Do you think google lock adds additional patches against modem AT attack against factory reset protection?
I personally visited Samsung Service Center where they used Samsung Galaxy Must. I tested with the same phone as above which is wipe out data/wipe out cache/reboot in recovery mode and which is google locked. As you remarked, “Must” unlocks in approximately 1 minute. If “Must” uses this modem “AT” commands, “Must” cannot change frp unlock in locked situation.
I am confused. I hope you have clearer perspective about modem “AT” in presence of frp.
Best regards,
Ingyu Koh
Comments are closed.